Threat Hunting: Get Started
Introduction
Threat hunting (detecting and finding things that you weren't previously aware of) has been around for a long time and most 'medium maturity' organizations will attempt to set up some form of threat-hunting activity or program but will find themselves stuck thinking about all the super cool advanced stuff and end up not actually really doing anything at all. So, I've created this blog post to help get people on track to actually develop something for their organization.
Why bother?
You and your organization should be doing threat hunting because at its heart it is just an application of a foundational concept within cybersecurity. Understanding what is going on in your consistency. So, because of this, it's virtually impossible to not receive a return on investment. Start a hunt and find you haven't been collecting logs for the last 6 months? Great! that's a positive output from threat hunting! Start a hunt and find more shadow IT than you can shake a stick at? Great! that's a positive output from threat hunting! Start a hunt and don't find anything of particular interest? Great! not only have you increased the assurance that your consistency is protected but you have probably improved or reinforced the soft and hard skills you used during the hunt, that's a positive output from threat hunting!
So, you see the reason why you should bother is that you will literally always stand to gain. Of course, finding undiscovered threats is probably going to be your primary motivator but you will naturally gain so much more around that.
How to get started?
Probably the best descriptor for getting started in threat hunting is "making lemonade from lemons" because at the start of your journey all you're going to have is you and your hypothesis nothing else really matters. So below are the exact steps you need to get started:
- Go explore and enumerate all the places where you store security-related data/information and document them. Include in that document any references to how you access/manipulate the data/information stores and exactly what type of security-related data/information they hold. You can do this in excel if you have nothing else.
- Start to think about something you want to find in the data/information you have enumerated in the prior step and write out a hypothesis. You can just pick out something from some security blog or identify a technique from MITRE ATT&CK®. It's important you do a little bit of sanity checking on your hypothesis so make sure you're not looking at MAC artifacts in a non mac environment etc.
- Start hunting! This part sounds the hardest but is actually the easiest. The expectation here is that you write some form of query that roughly matches your hypothesis at a high level. The quality of the query (accuracy etc) doesn't really matter just make a start because once you have you can then start to pivot around your data/information. hone your query and therefore increase the quality of the hunt.
- Record your outputs. There are lots of different things and ways you can record your outputs but to start just cover these things. Create a word document and some headings if you have nothing else:
- What data sources you hunted over
- What resources you used to create your hypothesis
- Your hypothesis
- The queries you used
- The output of the queries
- Your own comments on what you found
- any actions you took like raising a config issue to a client
- Date and time stamp
Congratulations you are now thrunting.
Maturity
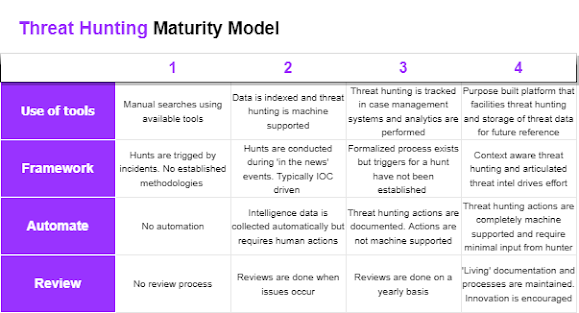
This blog covers the absolute bare minimum for threat hunting and the descriptor "making lemonade from lemons" should always be in the back of your mind because I see people dreaming big far too often. With that said you can increase in maturity from here. I've created a very rough chart that describes areas you can improve within a threat-hunting program:
In my opinion first and foremost when looking to increase the maturity of a threat-hunting program you should focus on the actual threat hunters themselves because it doesn't matter whether the threat hunter is using a yottabyte scale unified threat-hunting platform or writing scripts in COBOL it's their brains that ultimately generate the most valuable outputs. So, if you're just starting, ignore the above chart, and don't be afraid of using word, excel and scraped-together scripts and study study study.
On the topic of studying, you will find threat hunting is a very well-resourced domain, and there is lots of awesome content from lots of awesome people. You will find the most enjoyable stuff at all the different cons (literally every con has a thrunting talk) so try to dig up stuff on YouTube and keep your Calender full of invites to them. If you want more specific resources get a hold of me somehow and ill dig stuff up.
now go make lemonade out of lemons